Organizations across many industries are tasked with documenting their adherence to various regulatory requirements. From data protection laws like GDPR to industry-specific regulations, the compliance effort can be significant. In this blog post, we highlight some of the challenges and strategies for effectively documenting compliance with regulatory bodies. Read on…
Millennia Group Blog
Hype vs Understated
 Over the last 28 years, our company has consistently centered its mission on enhancing access to critical documents. Initially, this involved the conversion of paper documents into digital formats. Fast forward to the present, our commitment to facilitating better access remains unwavering. This dedication has manifested through the development and operation of FileStar, our proprietary software solution.
Over the last 28 years, our company has consistently centered its mission on enhancing access to critical documents. Initially, this involved the conversion of paper documents into digital formats. Fast forward to the present, our commitment to facilitating better access remains unwavering. This dedication has manifested through the development and operation of FileStar, our proprietary software solution.
Our evolution has been marked by simplicity and effectiveness. Transitioning from a predominantly service-oriented business to a software-centric model, our core focus on improving document access has remained constant. We’ve navigated the adoption of emerging technologies judiciously, avoiding the lure of hype while maintaining a measured pace of growth.
General Model means General Results

Artificial Intelligence (AI) and Large Learning Models (LLMs) are widely recognized in the business world for their transformative potential. What stands out in the numerous reports about these technologies is the diversity of models being developed. These models come in various forms, such as socially conscious models, math-oriented ones, those specializing in science, and even models with a sense of humor.
The existence of different models implies that there are influencers or factors shaping their distinctions. These influencers can be human, affecting the way algorithms are designed or the inclusion of certain guidelines. These influences often reflect the values and ideals of the model’s developers. While it’s important to filter out hateful or unsafe content, the definitions of what constitutes hatefulness or danger can vary widely, leading to the creation of different models.
Given the stats, consistency rules
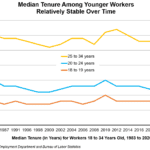
According to the Bureau of Labor Statistics Report of Tenure in 2022, the average tenure of all workers is 4 years. That number goes down to an average of 3 years for 25-34 year olds. If average tenure is 4 years, then a company of 200 has 50 employees turning over each year. Since your corporate human assets are replaced every 4 years, it makes sense why successful companies use process and process documentation where-ever possible. Otherwise, 1 in 4 employees could be making questionable decisions based on whatever limited information and spotty business records that they found.
However, a business process doesn’t provide new employees with answers, it provides the path to find the answers. But what if the process is only loosely followed. Guess what, the process fails because the “path” doesn’t stay consistent. This is one reason that ERP’s and CRM’s have taken hold and proved so successful. Those solutions can force the process to follow a consistent path with consistent required data.
Fatherly advice. Get back to the office.
I’ve been in the working world for long enough to have some credentials – 38 years to be exact. If I was advising my children, I would strongly suggest that they get back into the office as many days a week as possible and especially on Friday. As a father, I believe that is good advice for younger workers.
As a business owner whose company provides a cloud workflow and critical document archive solution, that could be shooting myself in the foot. The more people who work remotely, the more demand there is for businesses to have great solutions for remote workers to be productive. But I think my fatherly advice is the correct advice overall and here’s why.
Continue reading “Fatherly advice. Get back to the office.”Endnote, what’s that?

The internet is amazing and it seems will shortly be even more amazing when Bing and Google fully deploy their AI powered search engines. Finding information quickly is already simple and fast, especially if you have a pretty good idea of what it is you are looking for. When AI enters the picture, the picture literally could be significantly better.
Simple and fast search is great. But the degree of trust in the search result is based on the effort you make to get comfortable with the answer. A few clicks to alternative information maybe or just some level of trust in the source website. As the level of sophistication and depth of the questions being asked of AI increase, so too will the degree of trust needed in the result. And hence the need for endnotes.
Continue reading “Endnote, what’s that?”No Top Ten. Bottom Five.
Everyone does a top ten best or ten most list, especially at the beginning of the year. Top ten this or top ten that. But what about the bottom? What would that look like if we had the bottom five; five lowest played songs of 2022, five business ideas that fizzled by mid-year, five worst investments of 2022. That last one is real.
Can it help us to understand the five worst of something? Yes, absolutely that can be very helpful if for no other reason than to raise awareness. So here is a hypothetical list of five worst business operation decisions of 2022:
This is Critical
What’s your company’s superpower? It could be a technology, a marketing edge, engineering talent, or exceptional service. Whatever your secret sauce is, it’s important in generating your revenue. What could be its kryptonite? Obviously, whatever could harm or stop your superpower would logically be your kryptonite.
It’s also obvious that you want to prevent kryptonite situations from occurring. You visit important customers frequently, pay a lot for marketing and engineering talent and invest in your technology and operations. But somebody always wants to see proof. You do have the critical documentation, right?
Continue reading “This is Critical”Go ahead, take two weeks off
Banks and other financial institutions have a requirement that all officers must take two consecutive weeks off work. The reason, which is advocated by the FDIC, is so that the institution has a better chance to uncover fraudulent activity. If the employee is gone for an extended period, strange correspondence and irregular transactions handled by the backup employee could expose the fraud.
However, irregular and strange don’t only relate to fraud. That type of activity can be related to current business processes. Our last post was about how costly exceptions to the standard business process seem to go unnoticed because managing the exception becomes routine for that employee. Therefore, whenever there is employee turnover or extended PTO, plug in a trusted squeaky wheel and take notes.
Continue reading “Go ahead, take two weeks off”Workplace Bias, the Process Kind
We love to dig into our client’s business processes and help them overachieve their stated goals of improved efficiency or compliance. It’s a mentally challenging and stimulating exercise that we really enjoy. However, we have learned that part of the challenge is the fact that there’s a real bias to under-divulge information about what the current process consists of.
This bias is not intentional by any means. It’s a function of unconscious acceptance of exception management as part of the job. Put more simply, most employees just handle the issues that come up when there is an exception, and it doesn’t register as a “step” in the process. However, it is exactly these exceptions that take the most time and therefore cost the most money. Therefore, eliminating the bias to get to the true process is a great place to start.
Continue reading “Workplace Bias, the Process Kind”Mission Not Impossible
It’s difficult to claim that you are compliant with internal or external rules and regulations if you don’t have a good base to start with. Take the concept of the accurate value of your customer contracts for instance or exposure due to vendor contracts, both part of any Sarbanes Oxley regulations (SOX). It’s hard to imagine having complete confidence in those values or exposures, defined as no more than 5% deviation by SOX, if you don’t have confidence in the collection of supporting documentation.
The focus on customer contracts should take precedence and probably does already in terms of recording the contract terms in your billing system. But the effort for the most part is still a manual data entry process unless it’s a B2C relationship and all executed digitally online. Having those contracts to support the revenue is still very likely a messy, disorganized affair with some digital and some paper, some in the cloud and some on the network or attached to the ERP. An impossible task to corral it all right?
Continue reading “Mission Not Impossible”Match made in heaven

When two people seem very happy together, it’s “a match made in heaven.” When something just works exactly as you expect it to, you will hear someone say “bingo” or “the stars aligned.” More recent versions of this would include “life is good.” They are all just sayings that express the fact that something went right.
We won’t provide examples of common sayings when things go wrong. That could be humorous, or it might offend some people. Your employees should have “life is good” moments daily to the point where its just the way it is. They should quickly find a document that someone requested at the very end of the day. They should pull a collection of documents together that support an important compliance report in minutes not hours or days. How do you get there?
Continue reading “Match made in heaven”Not so fast with “bring on the auditors”
As a follow up to our last post about having a system of record to make audits seem like a walk in the park, there is more to it. Recall that a system of record document management solution holds the confirmed supporting documentation for your critical company data, such as, transactions, client accounts, vendor contracts, etc. If your current file storage solution is not working and you want to convert it to a system of record there are a few things that are required.
Like all good things, it will take some effort on the front end. But as we stated in the last post, it is well worth it. And the value is more than just having a better audit experience. Its worth it because you also have better information at your fingertips and that leads to better decisions. So what’s required? Be humble because you will likely learn that your organization is not perfect, be diligent and have some fun because you will discover nuggets of gold.
Bring on the auditors!
Does the thought of going through an audit scare you? What is an audit? According to The American Heritage Dictionary, an audit is – An examination of records or financial accounts to check their accuracy or confirm adherence to policy or regulation. And what does an auditor do? Performs verification and substantiation procedures. And what types of audits are there? Financial, compliance, internal, security and many more.
Audits are not something that most of us enjoy going through. Not for nefarious reasons, but mostly because of the extra time demands and that feeling of uncertainty about providing the required information. Your accounting system or ERP has been designed to collect and keep your transaction information. However, can your auditor verify and substantiate the transactions or adherence to policies by matching it to your supporting documentation? If not, you need to take a system of record approach to documentation and you’ll say “bring on the auditors”.
You need a smaller house
Has anyone experienced the dad who angrily says ‘where’s my screwdriver’, because it wasn’t put back where he thought it should be. Are some of your family members more organized than others? Is one more detail oriented or creative or devil-may-care? Maybe if your house was a lot smaller, say one room, you wouldn’t have this problem.
Ok, blow that up by 1,000 work associates and think about your critical information. You can’t make that “house” smaller. No HR department can choose work associates who all think and work alike. And you can’t effectively force a single method. What can be done to give users a reasonable chance to avoid wasting time looking for that screwdriver? Or more importantly, avoid a negative compliance or audit situation.
Continue reading “You need a smaller house”